Information Security Product Series
Asset Security Risk Management, Container Security Monitoring, SSL Security Gateway, Integrated Security Gateway, Threat Protection Gateway, Application Control Security Audit

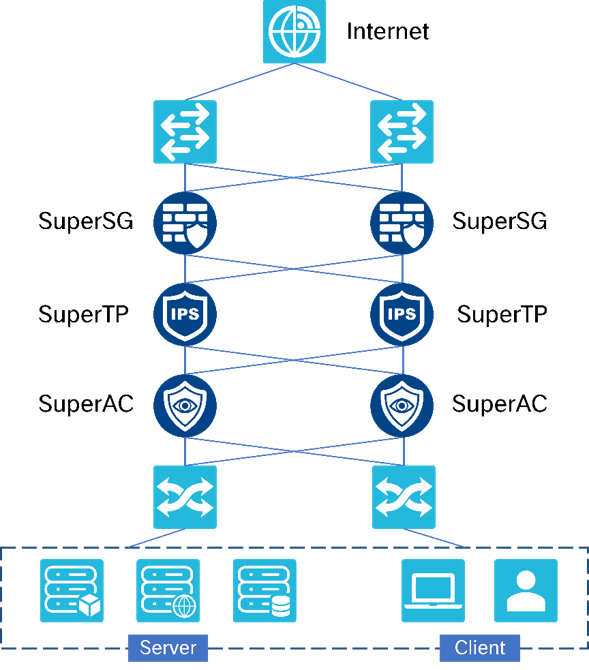
Hongji Technology's SuperTP series threat prevention gateway products adopt the latest multi-core multi-processor technology and combine with the independently developed SPOS operating system to compensate for the shortcomings of firewalls. They can effectively monitor all real-time transmitted data on the switch and provide comprehensive detection. As a security supervision and management tool, the intrusion detection system can provide users with comprehensive information presentation, providing decision-making basis for improving the risk control environment of user networks.

Warning in advance:The system can timely detect the occurrence of intrusion attacks before they cause harm to the network system and issue alarms
Defense during the incident:When an intrusion attack occurs, the system can promptly discover it and use TCP Killer and other methods to issue alarms and dynamic defense
Post-incident forensics: After being attacked by an intrusion, the system can provide detailed attack information for convenient forensics analysis
The SuperTP series threat prevention gateway adopts the independently developed SPOS super parallel processing architecture, enabling full parallel processing of the software pipeline and a single unpacking of the entire business process, resulting in a significant improvement in system processing performance. With multiple security defenses enabled, the system performance remains stable, ensuring the availability of business operations while reducing power consumption per unit of performance by 60% compared to similar products

The IDS utilizes protocol analysis technology to deeply understand known protocols and RFC specifications, enabling accurate and efficient identification of various known attacks. Meanwhile, based on the system protocol analysis algorithm, the sensor has the ability to detect protocol abnormalities and protocol misuse. The IDS currently supports more than 30 mainstream application-layer protocols, including Telnet, FTP, HTTP, SMTP, SNMP, DNS, and others
The IDS provides user identity recognition functionality by introducing the concept of user identification from next-generation firewalls into the IDS. With the continuous development of the network and the rise of BYOD (Bring Your Own Device), IP-based management is increasingly unable to meet the requirements of network management. User identity recognition links unseen IP addresses with real individuals. The IDS provides multiple user identification means to facilitate administrators better discovering threats and attacks

The IDS allows for flexible selection of security policies based on multiple factors, including security type, protocol type, system, level, event source, and others. Additionally, different defense levels can be defined for different security policies to apply various scenarios as needed