Information Security Product Series
Asset Security Risk Management, Container Security Monitoring, SSL Security Gateway, Integrated Security Gateway, Threat Protection Gateway, Application Control Security Audit

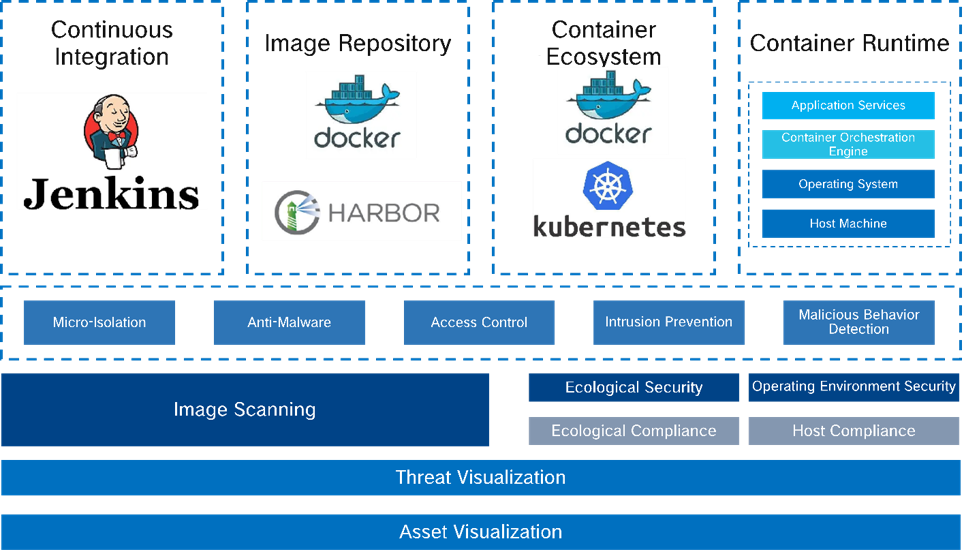
To address the protection of container environments and solve the pain point where traditional protections are only effective against host-based threats, the container security monitoring platform provides real-time monitoring and detection of vulnerabilities and viruses carried by container images, helping container images stay away from hacker infiltration and destruction threats. It allows for the setting of isolation between the host and containers, providing isolation based on layers such as containers, PODs, controllers, services, and namespaces to respond to east-west traffic security within the container. The platform also provides an asset visualization platform that synchronizes assets in real time and enables policies to take effect immediately, addressing the issue of asset management in the context of short container lif spans. It actively detects vulnerabilities to address the problem of frequent vulnerabilities in the container ecosystem.

Host Image Scanning

Container Invasion Monitoring

Compliance Check

Microservices Security Scanning

Container Network Security Monitoring

Repository Image Scanning
Provide container image security capabilities such as image threat detection, trusted image identification, and image runtime control
Address ecosystem security issues through host vulnerability detection and establishment of secure baseline configurations for the host and container environments
Provide proactive defense capabilities before intrusion, including the production and update of virtual patches to help patch vulnerabilities and mitigate 0-day exploits
Provide post-intrusion behavior detection and response capabilities, including real-time antivirus and WebShell detection, and defining a container access control behavior model
Provide a visualization platform that helps customers visualize their assets, identify security threats in real time through network and threat radar capabilities, and generate comprehensive security reports that facilitate better operation and traceability
Rule configurations require comprehensive understanding of system operations and can consume a lot of time. We can learn corresponding access models based on existing behaviors, fine-tune these strategies based on the self-adaptive behavior model, and save a lot of effort configuring policies

Directly kill ransomware, protect asset security in real time, block external network invasion packets, and audit attack operations, block escape actions, and audit escape actions
A single product to address host-container security, achieve unified management and unified solution, save resources, reduce conflicts, coordinate and collaborate to safeguard security, provide more comprehensive security protection, and be more suitable for hybrid cloud environments

In the face of security events, complete pre-analysis, in-process defense, post-event response, post-event audit, and ensure the security of the container system throughout its entire lifecycle

Supports both host agent deployment and containerized deployment methods, which can fully respond to complex scenarios such as distributed systems, hybrid clouds, and other container security scenarios